Analysis and Testing of Network Security for China Railway Communication Networks and Proposed Architecture Based on Trusted Computing
-
摘要: 为了保障我国铁路通信系统的网络安全,提出了一种基于可信计算和软件定义网络(software-defined networking,SDN)相结合的铁路通信网安全体系架构. 首先,从我国铁路通信系统网络整体架构出发,采用故障树分析方法,以“恶意人员造成铁路业务中断”为故障树的顶事件,对系统所面临的网络安全风险进行分析;其次,进行了仿真测试,根据测试结果拟合了一个恶意人员针对铁路通信系统的威胁场景. 通过仿真测试结果和分析表明,本文所提出的架构可以更好地应对大规模、针对性强的网络攻击行为,从而保障和提高我国高速铁路通信网络安全.Abstract: China’s railway communication networks have been deployed throughout the country and have a complex infrastructure. A security architecture based on trusted computing and software-defined networking (SDN) has thus been proposed for ensuring the security of the railway communication system. The security risks for the complete network were investigated and tested through fault tree analysis. A simulation evaluation was subsequently performed and a threat scenario was simulated for analysing possible intrusions into the railway communication network. The obtained results show that the proposed architecture can help address various organised, targeted, and persistent network attacks.
-
表 1 风险原因分类
Table 1. Classification of risk causes
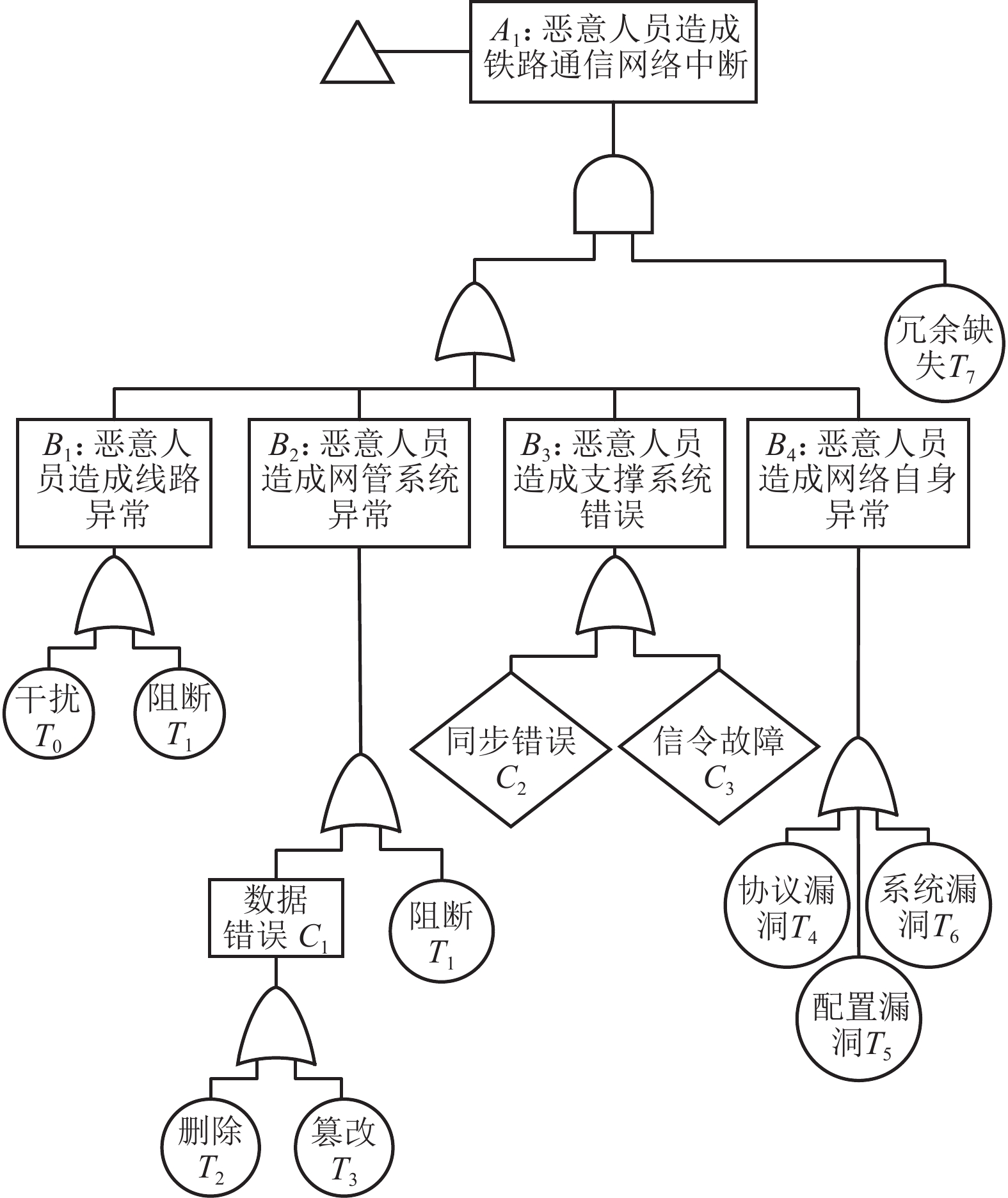
分类 原因 说明 数据错误 {T2,T3,T10,T11} 数据被删除、伪造、重放和篡改导致数据错误,影响业务可用性 系统缺陷 {T0,T1,T4,T6,T8,C2,C3} 通信链路(有线、无线)、网络、操作系统、应用软件和运维支持系统
存在可被利用的脆弱性人为失误 {T5,T9} 人为的配置错误(如采用弱口令、点击不明链接等);业务逻辑、
流程设计缺陷;安全策略缺失等冗余缺失 {T7} 没有冗余备份措施或失效 -
CARA M, LYDIA W. UK rail network hit by multiple cyber attacks last year[DB/OL]//The Telegraph, (2016-06-12)[2016-12-31]. http://www.telegraph.co.uk/technology/2016/07/12/uk-rail-network-hit-by-multiple-cyber-attacks-last-year/ 付淳川,王小敏,张文芳,等. 基于组件安全属性的列控中心信息安全风险评估方法[J]. 铁道学报,2017,39(8): 77-84 doi: 10.3969/j.issn.1001-8360.2017.08.011FU Chunchuan, WANG Xiaomin, ZHANG Wenfang, et al. A component security attribute model driven information security risk assessment approach for train control center[J]. Journal of the China railway society, 2017, 39(8): 77-84 doi: 10.3969/j.issn.1001-8360.2017.08.011 李赛飞,闫连山,郭伟,等. 高速铁路信号系统网络安全与统一管控[J]. 西南交通大学学报,2015,50(3): 478-484 doi: 10.3969/j.issn.0258-2724.2015.03.015LI Saifei, YAN Lianshan, GUO Wei, et al. Analysis of network security for chinese high-speed railway signal systems and proposal of unified security control[J]. Journal of Southwest Jiaotong University, 2015, 50(3): 478-484 doi: 10.3969/j.issn.0258-2724.2015.03.015 LGOR L, MARINA A. Cyber security analysis of the european train control system[J]. IEEE Communications Magazine, 2015, 53(10): 110-116 doi: 10.1109/MCOM.2015.7295471 WU Y, JIAN W, ZHE T, et al. Vulnerabilities,attacks,and countermeasures in balise-based train control systems[J]. IEEE Transaction on Intelligent Transportation Systems, 2017, 18(4): 814-823 doi: 10.1109/TITS.2016.2590579 RICHARD B, ROBIN B, ILIR G, et al. How secure is ERTMS?[C]//SAFECOMP 2012 Workshops. [S.l.]: LNCS, 2012: 247-258 郭伟,闫连山,王小敏,等. RSSP-II铁路信号安全通信协议的安全性分析[J]. 铁道学报,2016,38(8): 50-56 doi: 10.3969/j.issn.1001-8360.2016.08.008GUO Wei, YAN Lianshan, WANG Xiaomin, et al. Security analysis of railway signal safety communication protocol[J]. Journal of the China Railway Society, 2016, 38(8): 50-56 doi: 10.3969/j.issn.1001-8360.2016.08.008 LI S F, YAN L S, XING H L, et al. Enhanced robustness of control network for Chinese train control system level-3 (CTCS-3) facilitated by software-defined networking architecture[J]. International Journal of Rail Transportation, 2014, 4(2): 239-252 闫连山, 陈建译, 郭进. 铁路信号系统网络与信息安全[M]. 北京: 中国铁道出版社, 2016: 3-10 中华人民共和国铁道部. 铁路数字移动通信系统(GSM-R)总体技术要求: TB/T 3324—2013[S]. 北京: 中国铁道出版社, 2013 中国铁路总公司. 高速铁路通信技术-承载网[M]. 北京: 中国铁道出版社, 2013: 20-25 沈昌祥,张焕国,王怀民,等. 可信计算的研究与发展[J]. 中国科学:信息科学,2010,40(2): 139-166 沈昌祥. 可信计算构筑主动防御的安全体系[J]. 信息安全与通信保密,2016(6): 34-34 中华人民共和国国家标准. 信息系统等级保护安全设计技术要求: GB/T 25070—2010[S]. 北京: 中国国家标准化管理委员会 2011 孙瑜. 高安全级操作系统结构化关键技术研究[D]. 北京工业大学, 2011 Open Networking Foundation. Software-defined networking: the new norm for networks[DB/OL]. (2012-04-13)[2016-12-31]. http://www.opennetworking.org/images/stories/downloads/sdn-resources/white-papers/new-openflow-document.pdf 徐恪,朱亮,朱敏. 互联网地址安全体系与关键技术[J]. 软件学报,2014,25(1): 78-97XU Ke, ZHU Liang, ZHU Min. Architecture and key technologies of internet address security[J]. Journal of Software, 2014, 25(1): 78-97 徐恪,赵玉东,陈文龙,等. 防御数据窃听攻击的路由交换范式体系[J]. 计算机学报,2017,40(7): 1649-1663XU Ke, ZHAO Yulong, CHEN Wenlong, et al. Paradigm-based routing & switching system for data interception attacks[J]. Chinese Journal of Computers, 2017, 40(7): 1649-1663 -






 下载:
下载: