Efficient Privacy-Preserving Authentication Protocol for Mobile Cloud Computing Services
-
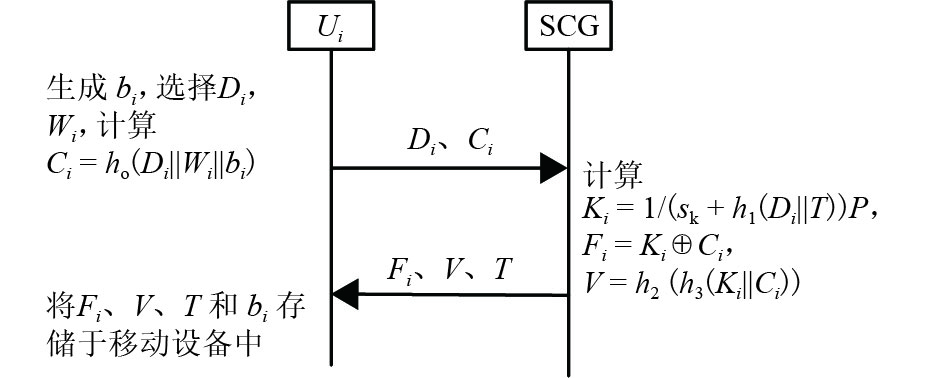
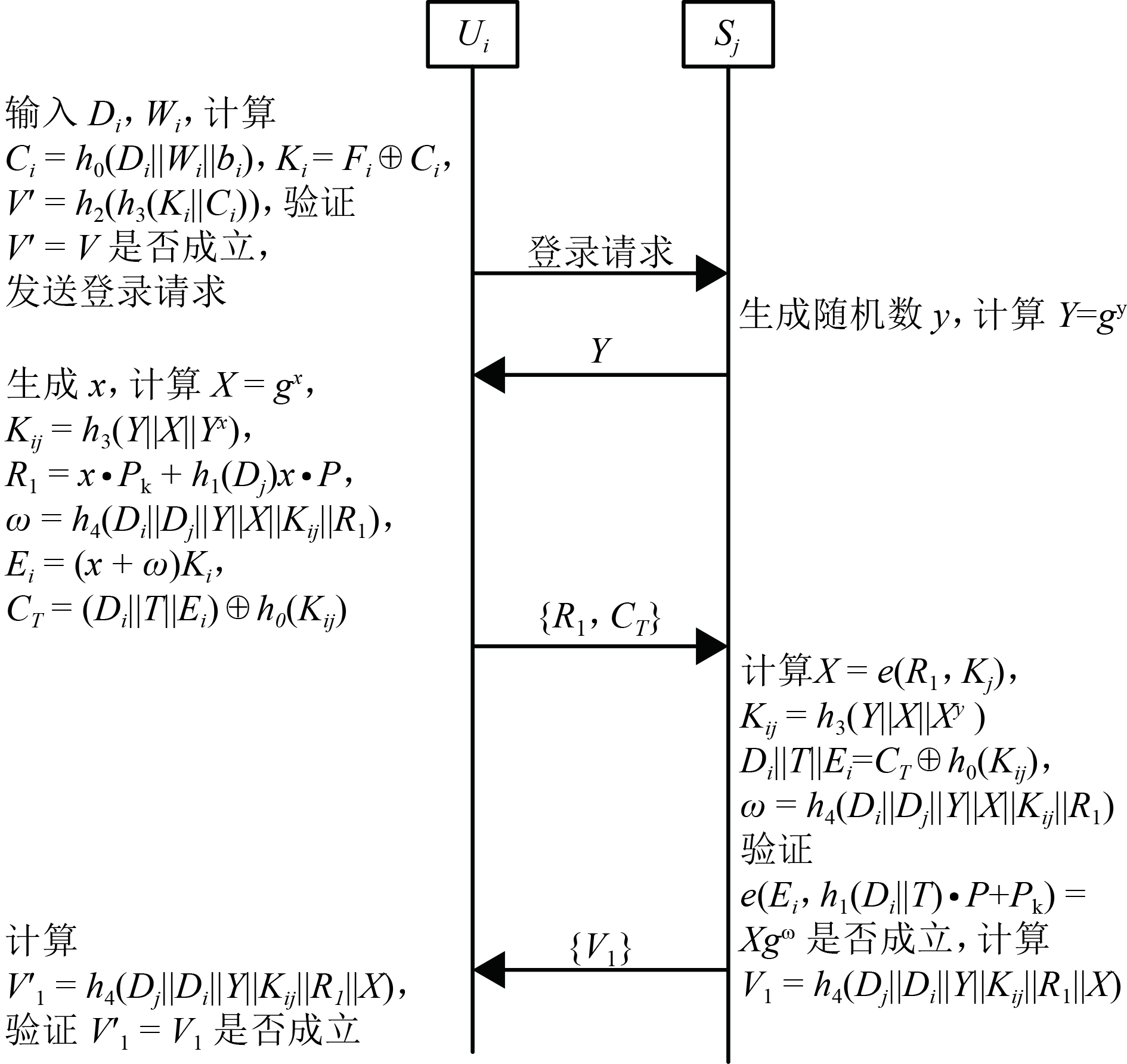
摘要: 为了解决移动云服务环境的互相认证和隐私保护问题,设计了一种改进的移动云服务环境下隐私保护认证协议.该协议结合基于身份的签密技术和多服务器认证技术,保证用户只需注册一次,就可以访问多个移动云服务提供者,同时认证过程不需要可信第三方参与;该协议在移动终端未使用计算复杂度高的双线性对运算和映射到域上的hash运算,其计算效率显著提高. 通过理论分析和实验结果可知:该协议与目前已有的同类协议相比,在移动端的计算时间为45.242 s,其计算效率约为已有同类协议的2倍;具有用户匿名和不可追踪等安全性质;能够抵抗错误口令登录、更改攻击.Abstract: To address the problems of mutual authentication and privacy preservation in mobile cloud computing (MCC) services, an efficient and provably secure privacy-preserving authentication protocol, based on an identity-based signature technique, is proposed for MCC services, achieving authentication without the help of a trusted third party. Additionally, because a multi-server authentication technique has been employed in the proposed scheme, mobile users can access all registered servers, which are registered only once at the registration centre. In the proposed scheme, time-consuming operations such as bilinear pairings and map-to-point hash are avoided in the resource-constrained mobile device. Thus, the running time of our scheme in the mobile device is 45.242 s, and the computational efficiency is approximately twice as fast as existing related schemes. Security analysis shows that our scheme can provide a variety of security features, such as user anonymity and untraceability. Moreover, it can resist wrong password loginand update attack
-
Key words:
- mobile cloud computing /
- authentication /
- privacy-preserving
-
表 1 安全功能对比结果
Table 1. Comparison of security functionality
表 2 相关操作运行时间
Table 2. Running time of related operations ms
时间 用户 云服务提供者 时间 用户 云服务提供者 Tmtp 33.582 5.493 Texp 2.249 0.339 Tbp 32.713 5.427 Tmul 0.008 0.001 Tsm 13.405 2.165 Th 0.056 0.007 表 3 计算性能对比
Table 3. Comparison of computation cost
方案 移动端 服务器端 Ref.[5] Tmtp + 4Tsm + Texp + 5Th + 2Tpa ≈ 89.893 2Tbp + 2Tpa + 2Tsm + 2Texp + 4Th ≈ 16.096 Ref.[16] Tmtp + 3Tsm + 3Texp + 5Th + Tpa ≈ 80.905 2Tbp + Tpa + Tsm + 3Texp + Tmul + 5Th ≈ 14.085 Ref.[17] Tmtp+Tbp + 4Tsm + 2Texp + 8Th + 2Tpa ≈ 125.023 2Tbp + 3Tpa + 4Tsm + 2Texp + 5Th ≈ 20.446 Ref.[18] 2Tmtp + 3Tsm + 2Texp + 5Th + Tpa ≈ 112.238 2Tbp + Tpa + Tsm + 3Texp + Tmul + 5Th ≈ 14.085 本方案 3Tsm + 2Texp + 8Th + Tpa ≈ 45.242 2Tbp + Tpa + Tsm + 2Texp + Tmul + 5Th ≈ 13.746 -
范平志,周维曦. 高移动无线通信抗多普勒效应技术研究进展[J]. 西南交通大学学报,2016,51(3): 405-417 doi: 10.3969/j.issn.0258-2724.2016.03.001FAN Pingzhi, ZHOU Weixi. Advances in anti-doppler effect techniques for high mobility wireless communications[J]. Journal of Southwest Jiaotong University, 2016, 51(3): 405-417 doi: 10.3969/j.issn.0258-2724.2016.03.001 中国互联网信息中心. 第39次中国互联网络发展状况统计报告[EB/OL]. (2017-01-22)[2017-06-20]. http://www.199it.com/archives/560209.html 李瑞轩,董新华,辜希武,等. 移动云服务的数据安全与隐私保护综[J]. 通信学报,2013,34(12): 158-165 doi: 10.3969/j.issn.1000-436x.2013.12.018LI Ruixuan, DONG Xinhua, GU Xiwu, et al. Overview of the data security and privacy-preserving of mobile cloud services[J]. Journal on Communications, 2013, 34(12): 158-165 doi: 10.3969/j.issn.1000-436x.2013.12.018 DELY P, KASSLER A, CHOW L, et.al. A software-defined networking approach for handover management with real-time video in WLANs[J]. Journal of Modern Transportation, 2013, 21: 58-65 doi: 10.1007/s40534-013-0007-x TSAI J L, LO N W. A privacy-aware authentication scheme fordistributed mobile cloud computing services[J]. IEEE Systems Journal, 2015, 9(3): 805-815 doi: 10.1109/JSYST.2014.2322973 JIANG Q, MA J F, WEI F S. On the security of a privacy-aware authentication scheme for distributed mobile cloud computing services[J]. IEEE Systems Journal, 2016(99): 4-7 刘辉,李晖,马占欣. 一个安全高效的车载网认证方案[J]. 西南交通大学学报,2011,46(2): 315-320 doi: 10.3969/j.issn.0258-2724.2011.02.023LIU Hui, LI Hui, MA Zhanxin. Efficient and secure authentication scheme for vehicular ad hoc networks[J]. Journal of Southwest Jiaotong University, 2011, 46(2): 315-320 doi: 10.3969/j.issn.0258-2724.2011.02.023 LEE S, ONG I, LIM HT, et al. Two factor authentication for cloud computing[J]. International Journal of KIMICS, 2010, 8(4): 427-432 CHOUDHURY A J, KUMAR P, SAIN M, et al. A Strong user authentication framework for cloud computing[C]//IEEE Asia -Pacific Services Computing Conference. Jeju Island: IEEE, 2011: 110-115 CHEN N, JIANG R. Security analysis and improvement of user authentication framework for cloud computing[J]. Journal of Networks, 2014, 9(1): 198-203 WANG R, CHEN S, WANG X F, Signing me onto your accounts through facebook and google: a traffic-guided security study of commercially deployed single-sign-on Web services[C]//Security and Privacy. San Francisco: IEEE, 2012: 365-379 Microsoft. Windows live ID[EB/OL]. [2017-03-11]. https://account.live.com/ OpenID Foundation, OpenID Authentication 2.0 [EB/OL]. (2007-12-05) [2017-03-11]. http://openid.net/specs/openid-authentication-2_0.html HUGHES J. Profiles for the OASIS security assertion markup language (SAML) V2.0[EB/OL]. (2005-03-17) [2017-06-20]. http://docs.oasis-open.org/security/saml/v2.0/ FETT D, KUSTERS R, SCHMITZ G. SPRESSO: a secure privacy-respecting single sign-on system for the Web[C]//The 22nd ACM SIGSAC Conference on Computer and Communications Security. Denver: ACM, 2015: 1358-1369 HE D, KUMAR N, KHAN M K, et al. Efficient privacy-aware authentication scheme for mobile cloud computing services[J]. IEEE Systems Journal, 2016, 99: 1-11 IRSHAD A, SHER M, AHMAD H F, et al. An improved multi-server authentication scheme for distributed mobile cloud computing services[J]. Ksll Transactions on Internet and Information Systems, 2016, 10(12): 5529-5552 ODELU V, DAS A K, KUMARI S, et al. Provably secure authenticated key agreement scheme for distributed mobile cloud computing services[J]. Future Generation Computer Systems, 2017, 68: 74-88 doi: 10.1016/j.future.2016.09.009 AMIN R, ISLAM S H, BISWAS G P, et al. A more secure and privacy-aware anonymous user authentication scheme for distributed mobile cloud computing environments[J]. Security and Communication Network, 2016, 9(17): 4650-4666 doi: 10.1002/sec.v9.17 WANG D, HE D, WANG P, et al. Anonymous two-factor authenticationin distributed systems:certain goals are beyond attainment[J]. IEEE Trans. Dependable Secure Comput., 2015, 12(4): 428-442 doi: 10.1109/TDSC.2014.2355850 WANG D, WANG P. On the usability of two-factor authentication[C]//Proc. 10th Int. Conf. Security Privacy Commun. Beijing: [s.n.], 2014: 141-150 MA C G, WANG D, ZHAO S D. Security flaws in two improved remote user authentication schemes using smart cards[J]. International Journal of Communication Systems, 2012, 27(10): 2215-2227 WANG D, WANG P. Two birds with one stone:two-factor authentication with security beyond conventional bound[J]. IEEE Transactions on Dependable and Secure Computing, 2016, 99: 1545-5971 MISHRA D. On the security flaws in ID-based password authentication schemes for telecare medical information systems[J]. Journal of Medical Systems, 2015, 39: 154-169 doi: 10.1007/s10916-014-0154-6 ODELU V, DAS A K, GOSWAMI A. A secure biometrics-based multi-server authentication protocol using smart cards[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(9): 1953-1966 doi: 10.1109/TIFS.2015.2439964 BRICKELL E, LI J. Enhanced privacy ID:a direct anonymousattestation scheme with enhanced revocation capabilities[J]. IEEE Transactions on Dependable and Secure Computing, 2012, 9(3): 345-360 doi: 10.1109/TDSC.2011.63 POINTCHEVAL D, STERN J. Security arguments for digital signatures andblind signatures[J]. Journal of Cryptology, 2000, 13(3): 361-396 doi: 10.1007/s001450010003 -




 下载:
下载:
 .
.
